What is Facial Morphing? How Can It Affect Identity Verification?
What is Facial Morphing?
Face verification technology has become increasingly popular in recent years, with many companies and organizations using it for security, fraud prevention, and identity verification. In more recent generations of smartphones, face verification has become a front-runner as the access technology for phone users. Lately, with the growing reliance on these technologies, we have started to see an increase in the use of facial morphing techniques. In this article, we will explore what facial morphing is, how it can affect identity verification, and what measures can be taken to counter it.

Source: Idemia.com
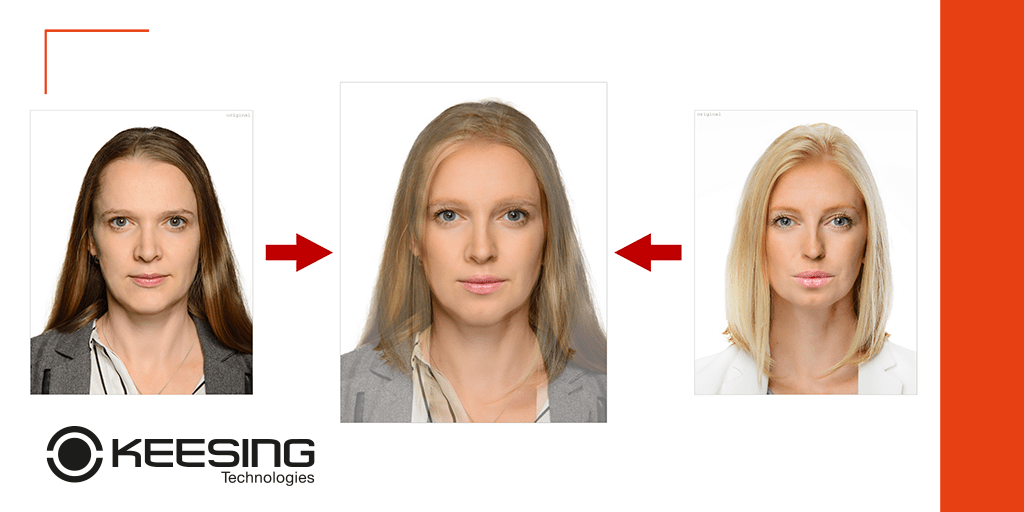
Morphing is about making changes: about introducing deliberate variation from an original image. As with all biometric technologies, face verification needs to handle a practical margin of error with any true face because variations of the facial image can occur for acceptable or unacceptable reasons. The acceptable include temporary changes to the face, aging of the face subject, or capture problems such as poor light conditions or camera quality. An important, but unacceptable reason is of course where the face just does not fit; it’s not the right person because it is a different face. Here, the technology is doing its intended job.
Typically, we measure the performance of biometric systems by their ability to separate a true face from a wide and various selection of untrue faces. The better system is the one most accurate at making the distinction. The concept of such comparisons is very static. With the emergence of morphing techniques, we must ask ourselves, how do we protect the truth of a face that is actively targetted by a technique able to play or experiment with the variation margin between true and false?
Facial morphing works by taking two or more images of different faces and using software to blend them. The false attacker image can be mixed with the true target image. The resulting image will have features from both faces, creating a new, composite face which, if successfully done can exploit the margin between true and false. It lives and thrives in this grey zone.
These techniques are often used for more dramatic cosmetic effects in the computer gaming and movie industries. Their success is in creating credible and realistic special effects which have since accelerated the possibilities of morphing for malicious purposes such as identity theft-based fraud. The first encounters with this technique were experienced with still images, but more recently the techniques have spread to the morphing of live, or streaming images, enabling the possibility of attacks on live video–based biometric encounters, and even fooling real people into giving away real money.
How Does Facial Morphing Affect Identity Verification?
Identity verification is a business process to confirm that an individual is who they claim to be. This process is crucial for security purposes and for verifying the identity of individuals for transactions as different as opening a bank account or applying for a new passport. Today biometric methods such as face verification play an increasing role here.
In an ID verification process, the attacker’s target is a known face. The attack might be designed for one-time use, or it might be part of a gradual takeover of a person’s biometric face. The problem for biometrics is no longer about performance within a large group of false samples: it is about detecting an active type of attack.
The problem goes in two directions. With biometric technologies there is always a matching process; two sides to the story. A live biometric image presented by someone wishing to verify their identity is compared with a reference image. The reference image may have been created years, months, weeks, or just days before it was first used for matching. The live image may be delivered in different ways but is always new. Some systems deploy forms of detection today to determine if the live image is created within the time of the verification transaction.
Real-Life Examples of Facial Morphing Attacks
The Morpher has two choices: experiment by attacking either the reference image or by attacking the live image. The live image is the popular choice because the reference images must be stored somewhere in a secure database or even a secure chip in an ID document, so access is tricky. Yet even this is a dangerous assumption.
Some years ago, an issuer of passport documents decided to ease the front office burden of its business by going along with an increasing trend to invite remote applications for passport renewals. On the face of it, this was a good, customer–friendly idea: easier for applicants and less burdensome for the passport office. The procedure was quite simple. Remote applications would only be available for renewals of documents under normal circumstances. The applicant would complete an online form and send a copy of their existing document along with a new digital face photograph. The photo on the document and the new photo would be compared with the original reference photo kept by the issuer from the original application some years before. If there was a positive match, the replacement passport would be issued. Considering the older age of the original photo then the new photo would become the one used for future biometric reference and in the new ID document.
This idea of this process was catching on fast until, in 2018, a German activist showcased the alarming potential of facial morphing techniques for identity impersonation by successfully creating a German passport that seems genuine. Leveraging sophisticated digital manipulation, the activist combined an image of Federica Mogeherini, who was the High Representative of the Union for Foreign Affairs and Security Policy at the time, with her photo. The passport application was approved, exposing the vulnerability of some passport issuance systems, and highlighting the serious consequences of such manipulation for identity verification processes. In this type of long-game attack, a false applicant could not only manipulate the live biometric data but also change the reference data over time in such a way that a false face could expect to impersonate the stolen identity successfully.
Long- or Short-Term Risk
Government ID providers work on long cycles, but within the commercial sector, an identity and its biometric might be created from new and then renewed more often. The rise of remote mobile onboarding systems is in many ways due to this high demand for identity verification. This brings with it the more frequent possibility of manipulating a face identity both by live impersonation, but also by morphing reference images that are presented to be closer to that of the actual impostors. A remote approach might present a facial selfie image and an image of a reference document, even a reference image stored in a fake document chip.
If morphed images are admitted to the reference data set for identity, when those forms of ID are used in human manual comparisons – such as border control – this will reduce the effectiveness even of trained face examiners to tell false from true, because the true reference data is no longer part of the presentation.
The diversification of government–based identities into different, and in some cases decentralized silos means that a morphed stolen identity could even live a long but parallel life with the true one, discovered only when evidence of fraud is revealed. A stolen identity can be for one day one-time use, or many years. Imagine finding that someone using your real identity, but with a morphed version of your face, has been opening bank accounts in your identity. If this attacker is smart, they will research you (by phishing your ID) to ensure they avoid a collision with your true ID. They can live in the shadow of your life.
Preventing Facial Morphing Attacks
Prevention is better than cure, so the first step is to take measures to prevent facial morphing attacks from happening. Here are some steps:
Use Liveness or Image Tampering Detection
Make sure that your face solution includes a component for Presentation Attack Detection (PAD). We do not offer an expert opinion on this here because there are many concepts involved and this is perhaps the most active area of development for face biometric technologies. In simple terms, liveness detection is a technology that can detect whether a face is real or fake. It works by analyzing facial movements and expressions to determine if the face is a live person or a static image.
Other forms of image analysis take a digital forensic approach to detect if an image comes from a single original source or is a composite object. These measures help to deter or prevent facial morphing attacks, but for remote onboarding, these methods are quickly becoming a standard requirement, mostly where the verification system makes limited checks on the reference document or facial reference data. Increasingly, we can expect more digital watermarking checks on images to detect later morphing manipulation and substitution.
Implement Multi-Factor Authentication
Multi-factor authentication is a security measure that requires users to provide more than one form of identification to access a system or account. By implementing multi-factor authentication, it can make it more difficult for attackers to gain access to sensitive information or carry out fraudulent activities. For identity onboarding additional authentication factors can be proper document verification checks, either of the visual aspects of a document or of the data presented by the document chip. Chip data checks should always include the verification of the issuer’s digital signature because remote attacks with false chip technologies are relatively easy to do.
Remember that Remote Authentication is for Convenience
Remote authentication is the dominant model for a digital networked world, but the assumption that this is sufficient because it is convenient and quick to use is a dangerous one. As the passport case illustrates, having a foundational model that relies upon the remote digital model runs a significant risk of corruption not only to the value of trusted transactions but to the whole concept of reference ID data.
The best safeguard to this is to ensure that the start of digital onboarding begins with a proper check on a person’s reference data, presented by a verifiable government ID, and to make an in–person check on the ID holder’s face biometric. This process should be repeated at intervals appropriate to the identity fraud risks involved. Periodic face-to-face attendance for such a process is not only a strong, multi-factor approach to fraud detection, but it is also the most secure front door to using digital biometric identities safely and securely.
The Future of Facial Morphing and Identity Verification
Facial morphing attacks are becoming more sophisticated, making it challenging to detect and prevent them. However, there are also advancements being made in facial recognition technology, such as 3D facial recognition, which can help prevent facial morphing attacks.
3D Facial Recognition
3D facial recognition technology uses depth-sensing cameras to capture a 3D image of a person’s face. This technology can be more accurate than 2D facial recognition, as it can capture more details and is considered by many to be less susceptible to facial morphing attacks. Considering today that most face reference data is held in a 2D format, then it will be a gradual process for this technology to upgrade both live and reference sides of the biometric matching process. It will also most likely lead to some market reorganization for biometric technologies.
Biometric Fusion
Biometric fusion is a technology that combines multiple biometric identifiers, such as facial recognition and fingerprint scanning, to verify an individual’s identity. By using multiple biometric identifiers, it can make it more difficult for fraudsters to bypass identity verification processes. This can be seen as a biometric version of multi-factor authentication. In the remote mobile world, there is significant interest in the combination of face with voice biometrics.
Protect your Business with Reliable Identity Verification
Keesing Technologies is at the forefront of face recognition technology by establishing strategic partnerships with Mobai and Amazon Rekognition to stay ahead of fraudulent attempts. By leveraging advanced cutting-edge technologies, our robust ID document verification solution – Keesing AuthentiScan – is equipped to combine face morphing detection with ID document verification to provide a reliable identity verification solution, safeguarding against identity theft and fraud. In addition, Keesing DocumentChecker can be strategically deployed as your first and last line of defense against identity fraud. The comprehensive database contains essential up-to-date ID document information that supports you with manual ID checking.
Contact us via email, phone at +31 (0)20 7157 825, or simply leave your credentials by clicking the button below, our team will be happy to showcase the product.
Conclusion
Facial morphing is a growing concern in the world of facial recognition technology and the idea of remote identity onboarding. As attackers are becoming more sophisticated in their techniques, measures need to be taken to prevent facial morphing attacks. Implementing robust security protocols including liveness detection, multi-factor authentication, ID document checking, regular updating of facial recognition systems, and using watermarking techniques, can all help counter facial morphing attacks and protect identities.